Validate your security everywhere.
From code to AI workloads
Securin's Adversarial Exposure Validation platform brings AI-first insight to real-world threats, so you can validate your security everywhere. Including AI models and applications.
Trusted by







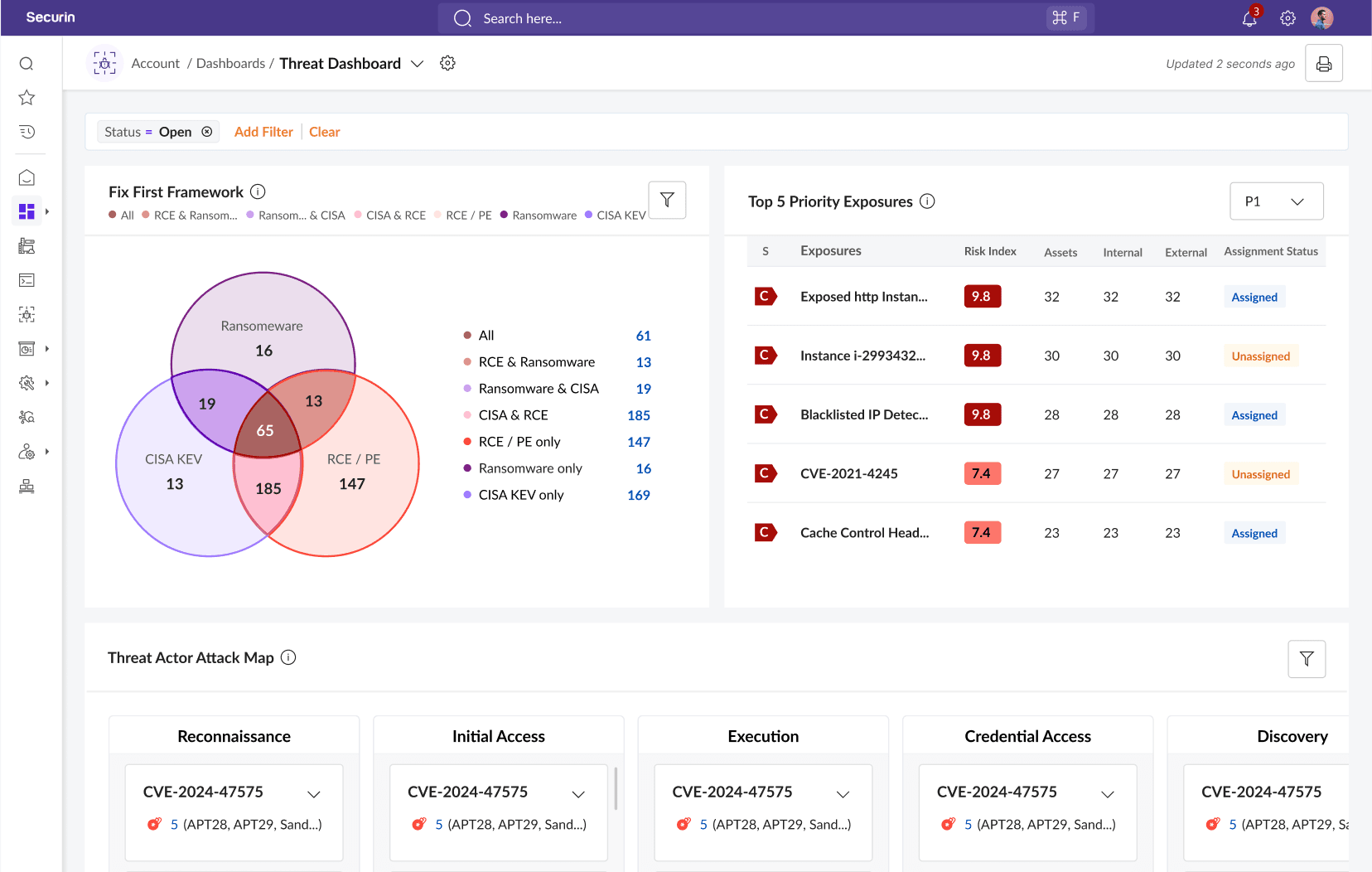
AEVOps: When attackers evolve at machine speed, validation must too.
Introducing Securin AEVOps - One unified platform
Adversarial Exposure Validation. Operationalized.
A ground-breaking, AI-first approach to adversarial exposure management. Our unified platform gives an adversary's view of your entire environment, so you can fix what matters most – and prove it worked.

Discover
See every asset, including shadow AI. Map real exposure pathways, not just inventories, so you see what adversaries will target first.
Analyze
Identify the attack paths that matter, using AI-driven exposure analysis across apps, infrastructure and models.

Validate
Test controls against real adversarial tactics, and confirm where defenses hold or fail.

Prioritze
Rank exposure by exploitability and blast radius, so the highest-impact risks for your environment rise to the top.

Remediate
Apply the right fix and automatically verify it worked - close the loop with evidence.
AI workloads. OT. IoT. Your entire infrastructure, secured and validated.
AI-first. Human-driven.
Actionable - always.
AI now attacks as fast as it protects.
Traditional security tells you what you already know.
Securin shows you what you're missing.
Automated Pen Testing
Bringing an attacker's perspective to your defense, validating exposure, reachability, defendability, and real-world risk - at scale. Securin's automated testing exposes the unknown unknowns hidden between tools and tests, revealing how adversaries could chain small gaps into real-world breaches.
AI Red Teaming
Securin's unique approach goes beyond simulation to reveal what traditional testing can't - the unknown unknowns hidden across both human and AI-driven attack paths. We don't just show what adversaries - including offensive AI - could do. We show you how they would do it.

Why leading education giant chose Securin
Schools are uniquely susceptible to pressure, and exceptionally vulnerable: underfunded, understaffed, and – unlike hospitals or banks – they lack the kind of hardened cybersecurity programs that soak up investment.
Continuous, Adversarial Threat Protection at Scale
A ground-breaking, AI-first approach to adversarial exposure management. Our unified platform gives an adversary's view of your entire environment, so you can fix what matters most – and prove it worked.
xxxx
xxxx
xxxx
xxxx
xxxx
xxxx
xxxx
xxxx
xxxx
xxxx
xxxx
xxxx
Events
Catch us at these events.
Us

We will be presenting at Riskcon25. Discussing our take on Adversial Exposure Validation

We will be presenting at Riskcon25. Discussing our take on Adversial Exposure Validation

The current state of ransomware: Insights from Riskcon25
Join the RAEVolution!
Continuous security across your entire environment
Built from 1500+ curated intelligence sources, and 1.58 million library components, Securin's unique data fabric correlates everything, eliminating the manual validation that slows you down and creates gaps in visibility. And when it's time to report on it, AI-powered insights have you covered, from every angle.

All Surfaces & Infrastructure

Controls

Actions
